
Mobile phone QR code

WeChat public account
According to the three documents including "DWA [2018] No. 10 Document" issued by the State Grid Corporation of China and the National Electric Power Dispatching and Communication Center' three documents, such as the notice on Printing and Distributing Standard for Grade Protection and Security Assessment of Power Monitoring System of State Grid Corporation of China (Trial), PV power stations and wind power station need to install longitudinal encryption devices between each PV square array/fan and the master station, so that the secondary security in the station can meet the "longitudinal authentication" requirements in the 16-character requirements of "security partition, exclusive network, longitudinal authentication and horizontal isolation", to ensure the safe data transmission between the data acquisition server at the booster station side and each photovoltaic array and fan.
According to the purpose of the above documents, our company has developed an overall solution for installing micro longitudinal encryption system in PV power stations and wind power stations. Our company starts to design the overall scheme from the view of the whole station, and designs the logical deployment location of the longitudinal encryption device, number of devices and basic technical requirements for the device as a whole.
Under the condition that the original communication topology of the wind power station is not greatly adjusted, the longitudinal encryption device is installed in the way of "hanging lanterns".
The following two figures are used to compare and explain the situation before and after installation:
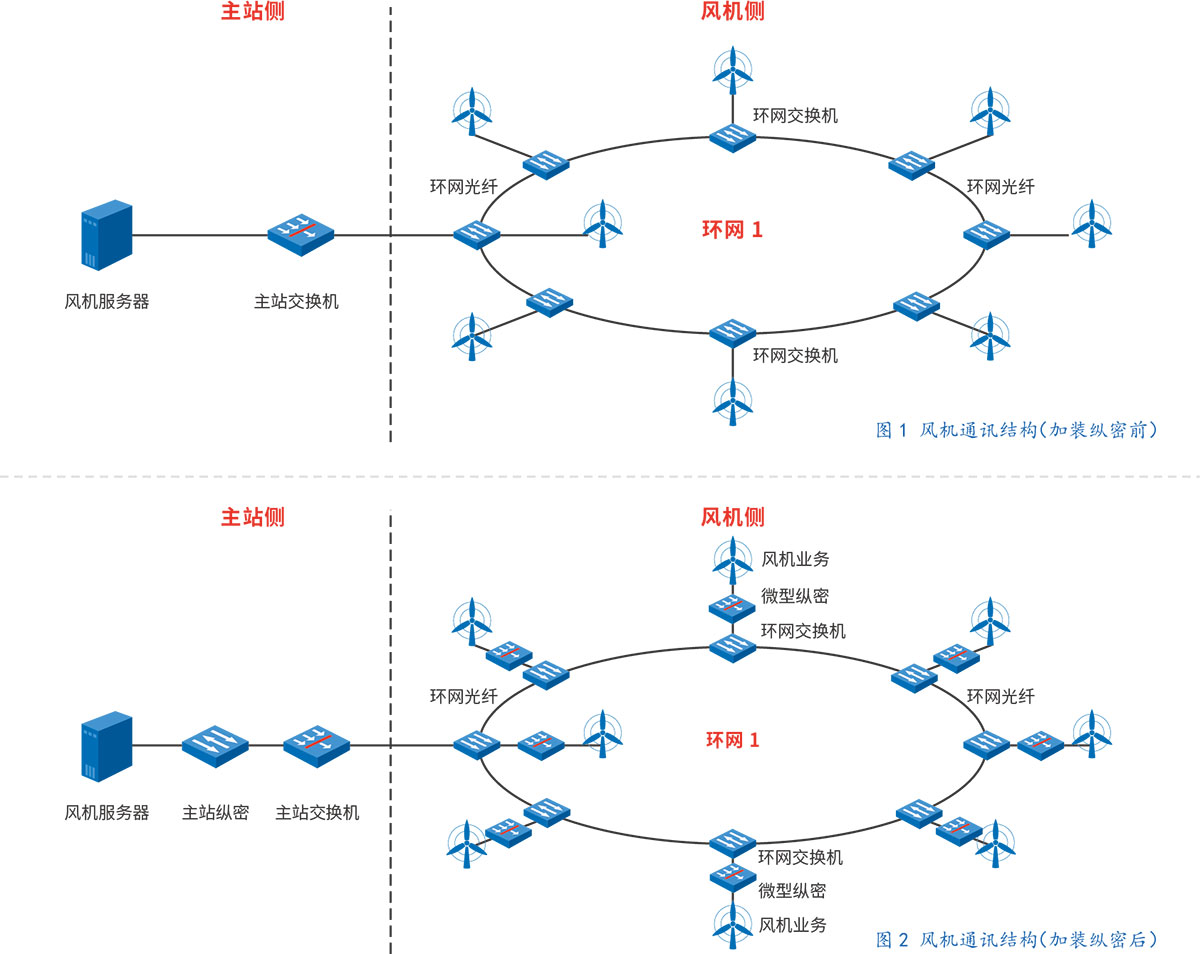
Under the condition that the original communication topology of the PV power station is not greatly adjusted, the longitudinal encryption device is installed in the way of "hanging lanterns". The following two figures are used to compare and explain the situation before and after installation:
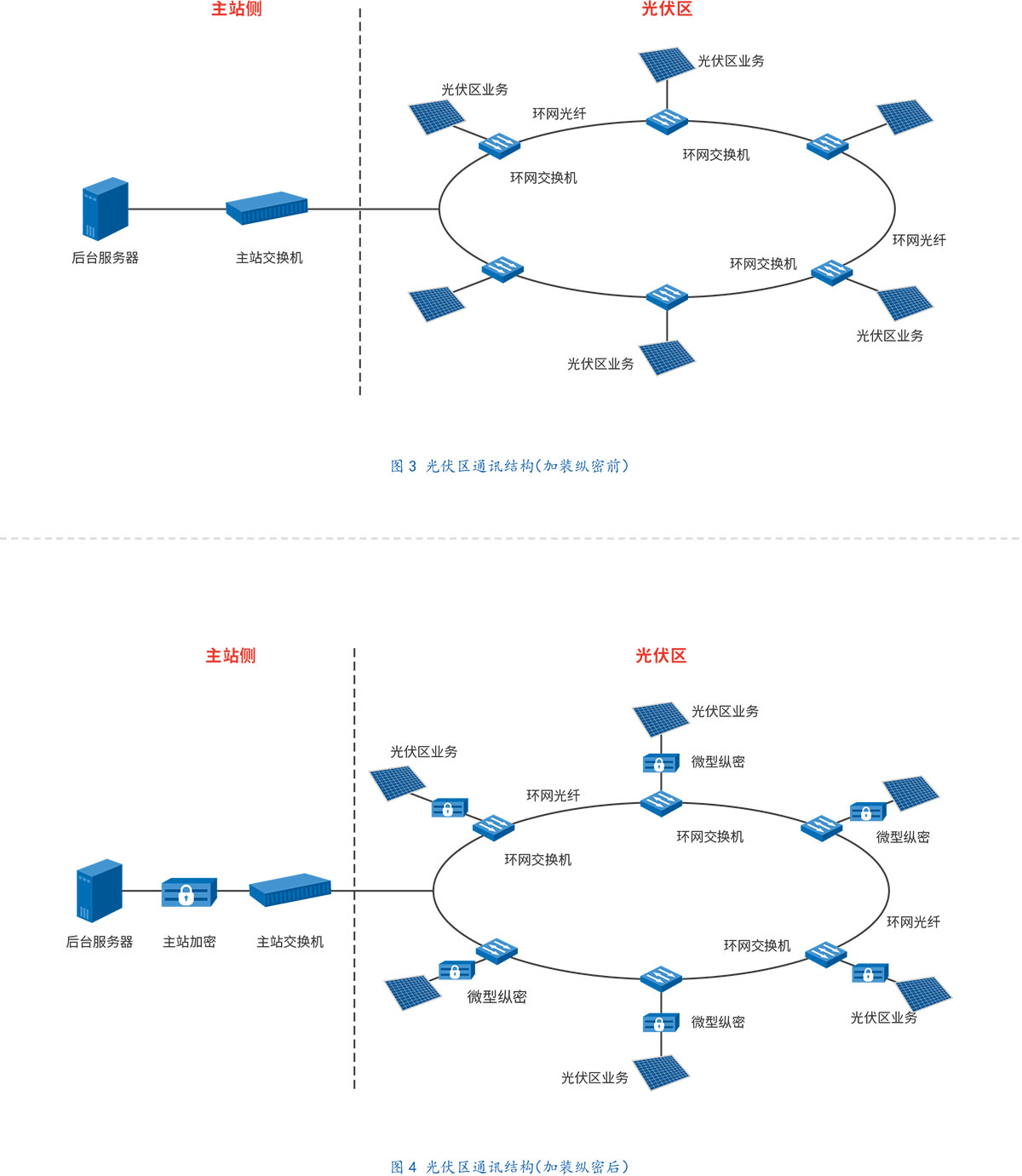
At present, the main manufacturers of longitudinal encryption and authentication equipment in China include Kedong, Xingtang, Nari and Westone, all of which have passed the test of the State Grid Corporation of China, and design products and interfaces according to the unified requirements of the State Grid Corporation of China. In view of the practical and widespread application of interconnection in the security protection of the power secondary system, the equipment of Beijing Kedong is introduced as follows:

Index parameter
|
Project |
PSTunnel-2000G (gigabit) |
|
Communication protocol |
IEEE802.3,TCP/IP |
|
Fault-free time |
100,000 hours (100% load) |
|
Transparency rate (1,024 bytes) |
≥1,200Mbps (50 security policies, and 1,024 bytes message length) |
|
Encryption rate (1,024 bytes) |
≥1,102Mbps (50 security policies, and 1,024 bytes message length) |
|
Number of tunnels supported (pairs) |
≥2,048 pieces |
|
Encryption time delay |
<1ms |
|
Number of network interfaces |
2*1,000M optical ports and 4*10/100/1,000M self-adaptive electrical ports |
|
Control port |
1 COM port (RJ45 form) |
|
Power supply |
2-channel 220V/50Hz AC input |

Index parameter
|
Project |
PSTunnel-2000T micro longitudinal encryption system |
|
Communication protocol |
IEEE802.3,TCP/IP |
|
Fault-free time |
60,000 hours (100% load) |
|
Transparency rate (1,024 bytes) |
≥70Mbps (50 security policies, and 1,024 bytes message length) |
|
Encryption rate (1,024 bytes) |
≥6.288Mbps (50 security policies, and 1,024 bytes message length) |
|
Number of tunnels supported (pairs) |
10 articles |
|
Encryption time delay |
<5ms |
|
Number of network interfaces |
2*100M network card interfaces |
|
Control port |
1 COM port |
|
Power supply |
DC wide voltage 9V - 36V power supply |
At present, the main manufacturers of longitudinal encryption and authentication equipment in China include Kedong, Xingtang, Nari and Westone, all of which have passed the test of the State Grid Corporation of China, and design products and interfaces according to the unified requirements of the State Grid Corporation of China. In view of the practical and widespread application of interconnection in the security protection of the power secondary system, the equipment of Beijing Kedong is introduced as follows:
The longitudinal encryption and authentication gateway provides a good monitoring function, which can monitor device status information, tunnel information, and security policy information based on the tunnel.
● Convenient connection and information feedback with the management center, many joint debugging with the development organization of management center, namely the "State Grid Corporation Information Security Laboratory", and full support for query and configuration of the management center. Rapid information feedback strongly supports the manageability of management center.
● Good online help effectively supports the operability for the user and the completeness of operation steps for the device.
● Longitudinal encryption and authentication device provides the log record for the operation and event, with a format fully in accordance with the "SYSLOG" specification. The log information includes time, event type and record content. The contents of the log can be respectively configured according to the needs of different users, and the log information is published and the corresponding alarm information is extracted through the "network port". The log information can be exported and backed up to the local hard disk.
● Provide the command to view the internal certificate information, and import the remote certificate information, such as local equipment certificate, operator certificate and management center certificate.
● Switch between the initialization state and the normal running state for the device. The management software can simply convert the initialization state of device into the "normal running state" through the "initialization guide" configuration.
● The "power longitudinal encryption and authentication gateway/device" with a special detection message similar to PING function, can indicate whether the security mode of the opposite side device is safe or bypass, whether the device status is normal or abnormal, and whether the device is main or standby.
● Support the monitoring and management messages sent by the management center. It supports the router trunk protocol. According to the needs of equipment access, the configuration and the driver supports of VLANID are required, and the resolution and the forwarding of two different bi-level Ethernet messages based on 02.1Q and Cisco standards are also supported.
The company has many years of experience in the operation and networking of protective communication equipment for wind power/photovoltaic projects, with a mature, complete and professional commissioning team, which can fully guarantee the on-site delivery and post-maintenance of longitudinal encryption authentication devices.
● The measurement and control of the box-type substation and the miniature longitudinal encryption are responsible by the same manufacturer, which is convenient for on-site debugging and post-maintenance of equipment, and avoids the connection with multiple manufacturers by the user.
● The on-site debugging of measurement and control for the box-type substation can be implemented together with installation and debugging of encryption device and optical fiber networking by our company, which can shorten the communication link between the two sides and speed up the project debugging progress.













